Towards Autonomous End-to-End Security in 6G
Introducing the ROBUST-6G Functional Architecture
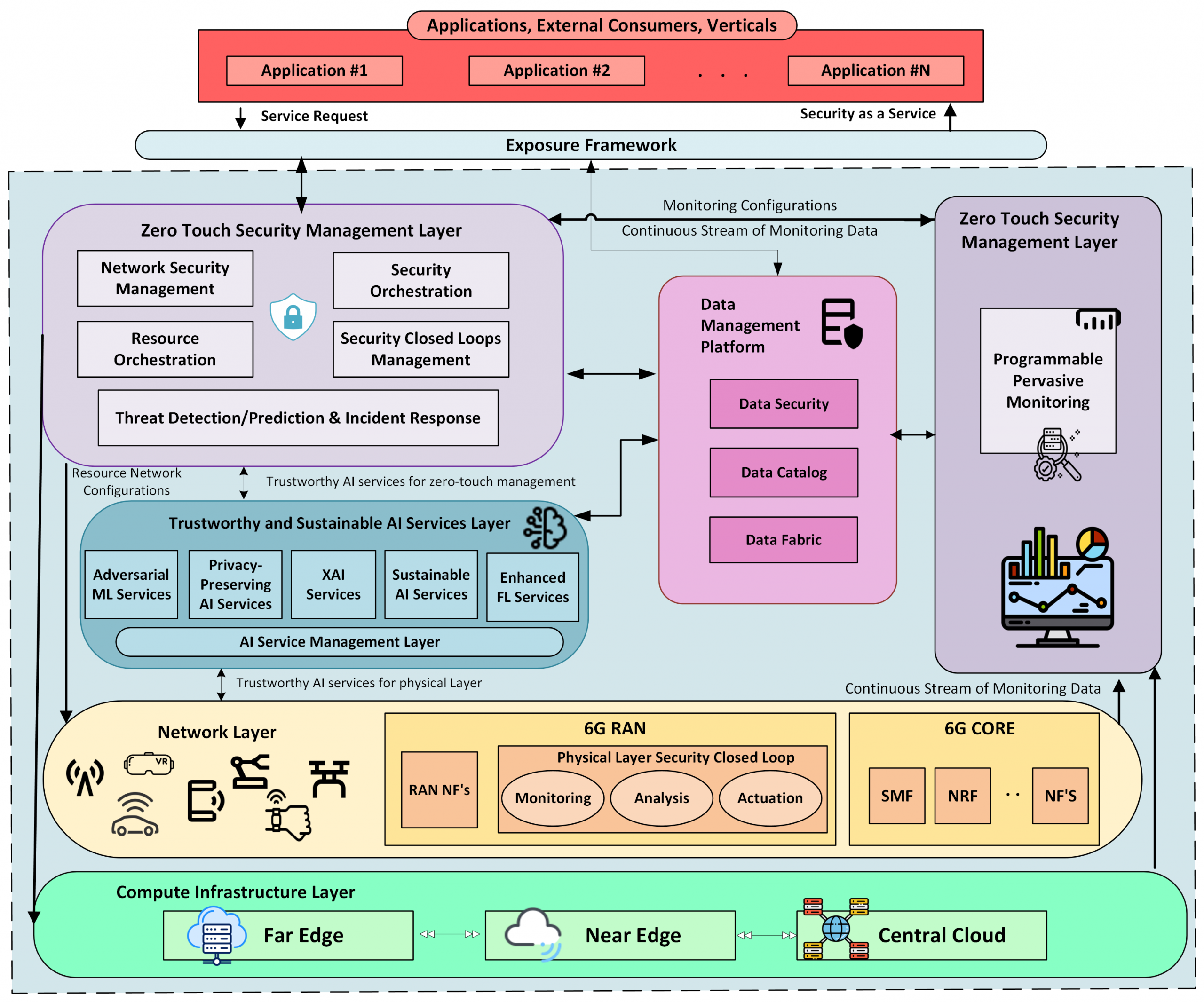
As Europe prepares for the next wave of wireless innovation, 6G networks will radically reshape how digital services are connected, managed, and secured. The ROBUST-6G project contributes to this transformation by developing an end-to-end (E2E), holistic security framework capable of supporting the extreme scale, intelligence, and flexibility of future 6G systems.
Our goal is ambitious: realize autonomous, zero-touch security for 6G, powered by distributed and decentralized trustworthy AI, secure data management, pervasive monitoring, and exposure of advanced security services to verticals and applications.
The ROBUST-6G architecture is built around modular, interoperable layers that together deliver proactive protection, fast mitigation, and cross-domain trust. This article presents a detailed overview of the project’s functional architecture and the role of each major layer.
Click on each layer to explore its role in the ROBUST-6G ecosystem.
Title
Exposure Framework: The Entry Point to 6G Security Services
The Exposure Framework forms the external-facing interface of ROBUST-6G. It connects the 6G network’s internal security capabilities with external consumers—vertical industries, developers, applications, and other domains—through secure and well-defined APIs.
Because of its openness and extensibility, the Exposure Framework ensures that ROBUST-6G’s advanced security intelligence is not isolated within the network, but actively usable by applications that require dynamic and trustworthy security guarantees.
The Exposure Framework enables:
- Enabling customization, for example integrating new services or onboarding domain-specific applications.
- Supporting use-case integration across industry verticals.
Its key functions include:
- Exposing security services such as threat insights, trustworthiness scores, anomaly reports, and policy management tools.
- Handling service requests such as invoking mitigation procedures or requesting security policy updates.
Programmable Pervasive Monitoring Layer: Continuous Awareness Across the Network
The Programmable Pervasive Monitoring Layer acts as the foundation of situational awareness for ROBUST-6G. It continuously observes the underlying infrastructure—whether running at the far edge, near edge, or central cloud.
It continuously collects:
- fault and performance measurements,
- incident reports,
- operational statistics,
- alarms or anomaly indicators.
This layer retrieves measurements directly from network functions (NFs) and infrastructure components, applying programmable monitoring logic that can adapt to new threats or emerging KPIs.
All collected data is forwarded to the Data Management Platform, enabling downstream layers to detect early warning signs, refine AI models, and automate mitigation.
Data Management Platform: Unified, Secure, and Distributed Data Control
The Data Management Platform (DMP) serves as the central nervous system for data within ROBUST-6G. It aggregates, secures, organizes, and distributes data collected from multiple layers of the 6G system. The platform handles data including:- physical-layer measurements,
- RAN and Core network telemetry,
- application-level metrics.
- managing secure data flow between sources and authorized consumers,
- enabling distributed data management across diverse 6G environments,
- enforcing privacy, integrity, and access controls,
- supporting metadata organization and discovery.
- Data Fabric — ensures interoperability across heterogeneous data environments,
- Data Catalog — enables structured data discovery and metadata management,
- Data Security — governs authentication, authorization, and confidentiality.
Zero-Touch Security Management Layer: Orchestrating Autonomous Protection
The Zero-Touch Security Management (ZTSM) Layer is the architectural “brain” coordinating security across the 6G system. It transforms traditional manual security management into an automated, intelligence-driven process capable of predicting and mitigating threats in real time.
Its main components include:
- Network Security Management – defines and enforces security policies and SSLAs,
- Security Orchestration – deploys and coordinates security functions across distributed nodes,
- Resource Orchestration – allocates compute/network resources for security operations,
- Security Closed-Loop Management – automates detection, analysis, decision-making, and actuation,
- Threat Detection/Prediction & Incident Response – uses AI/ML to identify, classify, and respond to attacks.
Through multiple autonomous closed loops, ZTSM can detect deviations, predict potential risks, and initiate corrective measures—all without human intervention. This automation is central to the zero-touch philosophy envisioned for 6G.
Trustworthy & Sustainable AI Services Layer: Making AI Reliable for 6G Security
AI is essential to the intelligence and automation of 6G, but AI-based security models must themselves be protected and trustworthy. The Trustworthy & Sustainable AI Services Layer ensures that all AI models used across ROBUST-6G are secure, interpretable, privacy-preserving, and resource-efficient.
It provides the following AI services:
- Enhanced Federated Learning (FL) — enabling training across distributed datasets without sharing raw data,
- Adversarial ML Services — protecting models from manipulation or adversarial attacks,
- Explainable AI (XAI) — ensuring transparency and interpretability of decisions,
- Privacy-Preserving AI — employing mechanisms such as differential privacy and secure computation.
Sustainable AI Services — enabling low-complexity model design, energy-aware training and inference, and resource-efficient AI pipelines across the edge–cloud continuum.
By combining trustworthiness, privacy, robustness, and sustainability, this layer provides the foundation for secure, responsible, and future-proof AI operations supporting Zero-Touch Security Management and Physical Layer Security in 6G networks.
Physical Layer Security Closed-Loop Layer: Protecting the Air Interface
6G introduces new threats at the physical layer, making Physical Layer Security an essential element of the ROBUST-6G architecture. This layer implements a local closed-loop system to protect the air interface.
The closed-loop integrates:
- Monitoring — gathering signal-level data from UEs and base stations (BSs),
- Analysis — applying AI/ML to detect physical-layer anomalies like spoofing, jamming, or abnormal channel patterns,
- Actuation — enforcing rapid mitigation, such as power adjustments, beam adaptation, or localized blocking.
Deployed close to the RAN—either within the base station or the edge node—this layer ensures ultra-fast detection and response to threats originating from the radio environment.
Conclusion: A Unified and Autonomous Security Framework for 6G
The ROBUST-6G architecture brings together programmable monitoring, secure data handling, autonomous orchestration, trustworthy AI, and physical-layer protection into a cohesive, end-to-end security solution tailored for 6G networks.
By integrating these capabilities under a flexible Exposure Framework, the project ensures that advanced security intelligence becomes accessible to verticals, developers, and applications across the 6G ecosystem.
ROBUST-6G lays the foundation for a future where security is autonomous, adaptive, and embedded across every layer of the 6G network—ensuring that Europe’s next-generation digital infrastructure is secure, resilient, and trustworthy from the ground up.