As 6G emerges as a transformative force in digital communication, its ability to seamlessly integrate the digital and physical worlds hinges on robust security frameworks. ROBUST-6G’s Deliverable 2.1, “6G Threat Analysis Report,” lays the groundwork for addressing this pivotal challenge, offering a comprehensive exploration of the evolving 6G threat landscape and strategies to mitigate potential risks.
The Importance of 6G Security
6G networks promise to revolutionize communication by supporting immersive applications like holographic telepresence, joint sensing, and communication. However, this innovation introduces complexities in managing and securing the network infrastructure. The ROBUST-6G project recognizes the criticality of a proactive approach to cybersecurity, aiming to protect network services, infrastructure, and data from an unprecedented expansion of threats.
Key Contributions of Deliverable 2.1
Comprehensive Threat Analysis
The deliverable offers a detailed state-of-the-art review of existing solutions for threat detection and protection, and an analysis of the characterization of security threats in 6G networks. It identifies technical synergies and gaps in existing frameworks, focusing on:
- Physical layer threats.
- Vulnerabilities in AI/ML modules.
- Risks in Application Programming Interfaces (APIs).
The analysis is performed on selected key 6G technical enablers, use cases and applications within a common framework on threat analysis.
Framework and Methodologies for Threat Identification
ROBUST-6G leverages established methodologies such as the CIA model (Confidentiality, Integrity, Availability) and Microsoft STRIDE to systematically identify threats. These frameworks are adapted to evaluate risks across diverse 6G technical enablers and applications.
The CIA model with the three security attributes Confidentiality, Integrity, and Availability, is a classical model used to describe and identify threats against assets (software, data, hardware, and humans) in a system. This model is also a part of ISO 27001 which defines security as being CIA. The CIA model is an asset-centric (or data-centric) model, where each asset can be associated with multiple threats and with multiple security attributes. The CIA model is often seen as an academic model since it does not offer enough guidance to practitioners when identifying threats to a larger system.
A more practical approach to identify threats is the method developed and used by Microsoft, the STRIDE method. It has extended the CIA attributes with authorization, non-repudiation, and authenticity to make it more guiding and useful when identifying threats. It also focuses on end results and threats and not on individual assets as the CIA model. Since a large complex system will have lots of components interacting with each other in complicated ways, this is a more suitable approach. It supports the creation of data-flow diagrams to see how data flows and how interactions between components occur.
The STRIDE method is easy to use also for non-security experts since it gives much better guidance than the CIA model. The method has a good track record and performs well when identifying threats and vulnerabilities in complex systems. The term STRIDE stems from the initial letters of six different threat types that should be considered when a system or function is analysed:
- Spoofing – attackers pretend to be someone or something else.
- Tampering – attackers change data in transit or in a data store.
- Repudiation – attackers perform actions that cannot be traced back to them.
- Information disclosure – attackers get access to data in transit or in a data store.
- Denial of service – attackers interrupt a system’s legitimate operation.
- Elevation of privilege – attackers perform actions they are not authorized to perform.
Focus Areas for Threat Analysis
The analysis delves into critical 6G technologies, including:
Distributed Multiple-Input Multiple-Output (D-MIMO)
D-MIMO is a core enabler of 6G, designed to meet the increasing demand for network capacity and reliability. By deploying multiple distributed antennas, it enhances area coverage and reduces interference.
Threats Identified:
-
- Spoofing: Impersonation of network components such as User Equipment (UE) or Access Points (APs).
- Tampering: Modification of fronthaul and backhaul traffic, as well as physical tampering with infrastructure nodes.
- Denial of Service (DoS): Attacks on physical APs or network links leading to service disruptions.
- Information Disclosure: Eavesdropping on weakly or unprotected data traffic.
Mitigation Strategies:
-
- Adoption of secure protocols with encryption and digital signatures.
- Implementation of tamper-resistant hardware and secure software updates.
- Use of Physical Layer Security (PLS) techniques such as RF fingerprinting to authenticate components.
Threat matrix on D-MIMO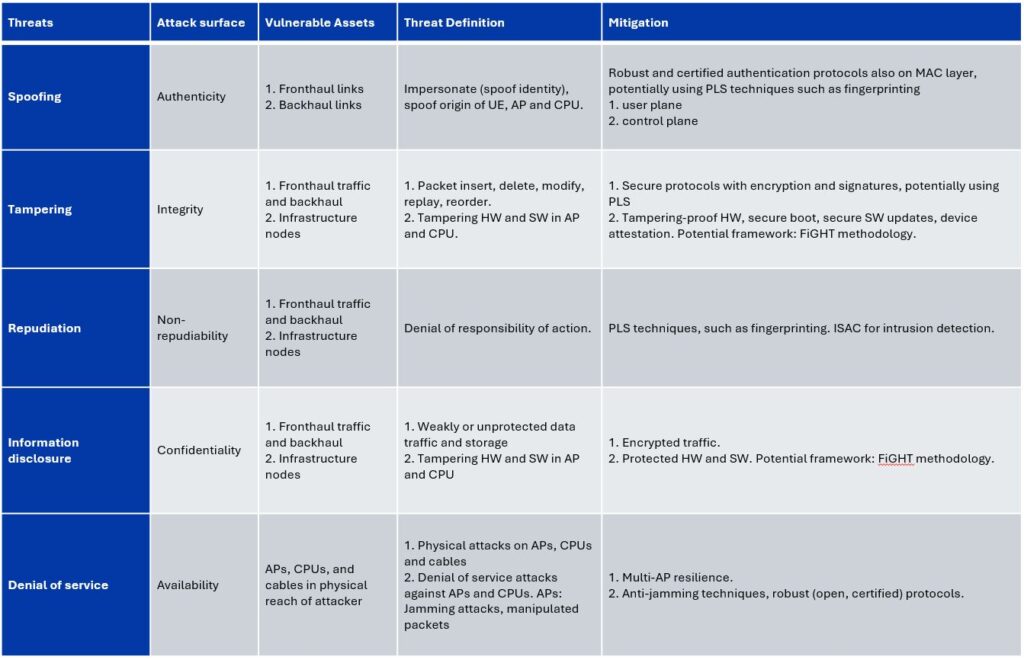
Reconfigurable Intelligent Surfaces (RIS)
RIS technology enables dynamic control of wireless signals, optimizing signal propagation through reflection, focusing, or modulation.
Threats Identified:
-
- Spoofing: Manipulation of RIS to induce specific channel characteristics for malicious purposes.
- Tampering: Injection of signals or malicious control of RIS to alter legitimate transmissions.
- Information Disclosure: Eavesdropping facilitated by unprotected RIS configurations.
- DoS Attacks: Exploitation of RIS vulnerabilities to disrupt operations.
Mitigation Strategies:
-
- Strengthening modulation and beamforming techniques to counter spoofing and tampering.
- Deploying hybrid RIS configurations with sensing capabilities to detect anomalous behavior.
- Using artificial noise and secure channel estimation to protect communication confidentiality.
Threat matrix on RIS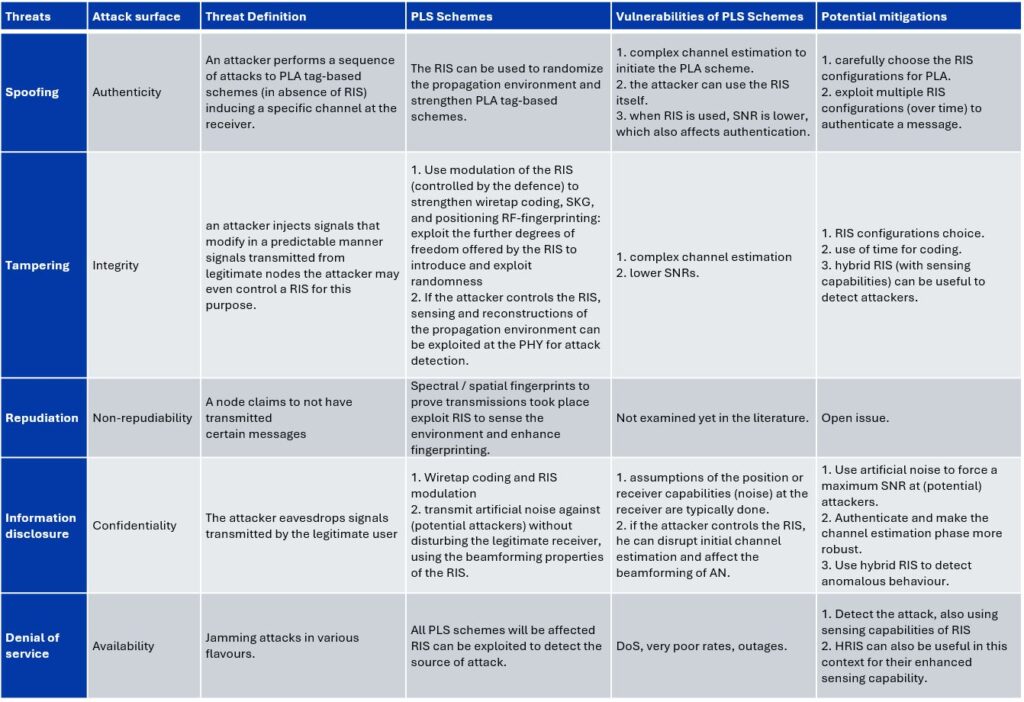
Millimeter Waves (mmWaves) and Sub-Terahertz (THz) Frequencies
Operating in higher frequency ranges, mmWaves and THz frequencies offer exceptional data rates but introduce new vulnerabilities due to their unique propagation characteristics.
Threats Identified:
-
- Spoofing: Adversarial nodes mimicking legitimate transmitters.
- Tampering: Injection of signals or disruption of channel state information.
- Information Disclosure: Eavesdropping due to narrow beamwidths.
- Jamming: Targeted interference leveraging the wide bandwidth of THz frequencies.
Mitigation Strategies:
-
- Wiretap coding and RF fingerprinting for authentication and confidentiality.
- Precise positioning-based security mechanisms leveraging directional communication.
- Development of geofencing and jamming mitigation techniques, including energy harvesting from jamming signals.
Threat matrix on mmWaves and sub-THz
Distributed Learning (DL)
Distributed and federated learning systems are key components of AI-driven 6G, enabling collaborative model training without centralized data storage.
Threats Identified:
-
- Poisoning Attacks: Injection of malicious data or updates to degrade model integrity.
- Privacy Violations: Extraction of sensitive training data or model parameters.
- Evasion Attacks: Manipulation of inference inputs to disrupt predictions.
Mitigation Strategies:
-
- Robust aggregation techniques like Krum and FoolsGold to detect malicious clients.
- Incorporation of differential privacy and homomorphic encryption for data protection.
- Blockchain-assisted distributed learning for enhanced security and accountability.
Internet of Things (IoT)
The IoT ecosystem within 6G will expand significantly, encompassing applications like healthcare, agriculture, and vehicular communication.
Use Cases and Threats:
-
- RFID in Smart Healthcare: Risks of data tampering and eavesdropping in RFID tags.
- LoRA for Agriculture: Vulnerabilities in chirp-based communication systems to spoofing and jamming.
- V2X Sidelinks: Challenges in authenticating and securing vehicle-to-vehicle communications.
Mitigation Strategies:
-
- PLS techniques, such as wiretap coding, to ensure confidentiality.
- Integration of sensor data (e.g., radar and cameras) for improved sidelink authentication.
- Real-time channel learning to adapt security measures dynamically.
Application Programming Interface (API) Exposure
API exposure is vital for enabling new use cases in 6G, transforming networks into programmable platforms.
Threats Identified:
-
- Spoofing and Tampering: Attacks on exposed APIs, leading to unauthorized access or manipulation of network functions.
- Information Disclosure: Leakage of sensitive data through API interactions.
- DoS Attacks: Overloading API systems with excessive requests.
Mitigation Strategies:
-
- Deployment of secure API frameworks like CAMARA, incorporating authentication and authorization mechanisms.
- Continuous monitoring and logging to detect and respond to anomalous activities.
- Encryption and secure transmission protocols to protect API data flow.
A Common Framework for Threat Analysis
The deliverable proposes a unified framework for evaluating threats, providing a basis for designing cybersecurity capabilities across ROBUST-6G’s technical work packages.
Path to a Secure 6G Future
ROBUST-6G’s efforts in Deliverable 2.1 emphasize the need for an integrated approach to security, aligning technological advancements with stringent protection measures. By combining AI-driven solutions, zero-trust principles, and innovative physical layer security mechanisms, the project paves the way for resilient and trustworthy 6G systems.
What’s Next?
This deliverable sets the stage for subsequent ROBUST-6G efforts, including the development of end-to-end security architectures and real-world validation. As 6G continues to evolve, ensuring its secure implementation will remain at the forefront of innovation, reinforcing the role of cybersecurity as an enabler of progress.
Stay tuned for updates on ROBUST-6G as we continue to push the boundaries of communication technology!
For more details, visit ROBUST-6G-Deliverables.