As 6G networks promise unparalleled connectivity with ultra-low latency, high bandwidth, and multi-domain interoperability, they also face an increasingly complex security landscape. The integration of advanced AI/ML-driven automation in network management introduces new opportunities but also heightens the potential risks of emerging cybersecurity threats. Addressing these challenges requires novel solutions prioritising end-to-end security while enabling seamless automation.
The ROBUST-6G project is pioneering efforts to develop a Zero-Touch Security Platform. This innovative framework ensures that 6G systems remain secure, adaptive, and reliable. Deliverable 4.1, the first major milestone of Work Package 4, lays the groundwork for this platform by identifying its foundational pillars and defining its preliminary architecture. This blog post delves into the highlights of this deliverable, emphasising the platform’s mechanisms, architecture, and vision for future implementation.
The Four Pillars of the ROBUST-6G Zero-Touch Security Platform
Deliverable 4.1 identifies four core mechanisms essential for achieving automated security in 6G networks. These pillars not only address the growing complexity of security management but also ensure adaptability in multi-domain environments.
1. Security Service and Resource Orchestration
Security orchestration in 6G is no longer limited to reactive measures; it now encompasses proactive and predictive orchestration strategies aligning with the concepts of preparation and incident response lifecycle provided by SP 800-61 Rev3 publication.
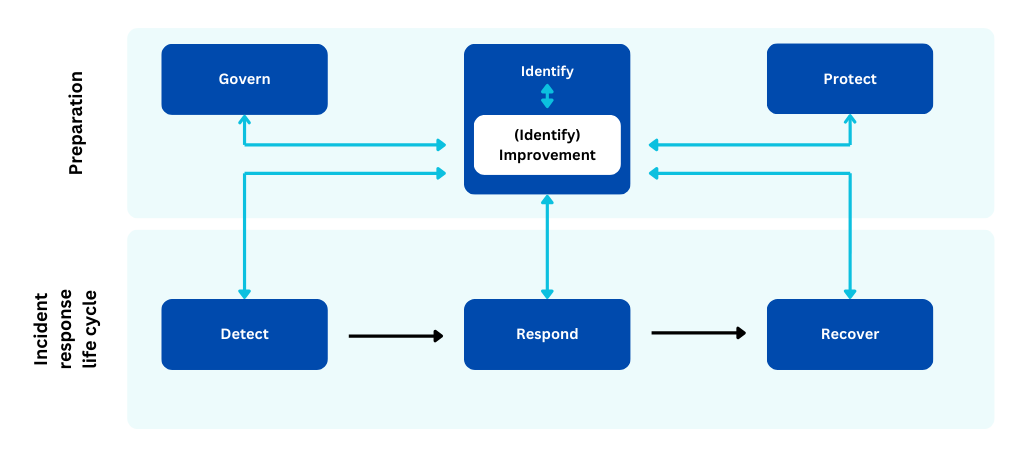
NIST SP 800-61 IRP
The Security Orchestrator is a central module that ensures seamless integration of security services across heterogeneous domains by automating their deployment, configuration, and management to meet dynamic network and security requirements.
Key highlights of this mechanism include:
- Real-time orchestration of security services to align with end-user policies.
- Automated remediation of policy violations and emerging security threats.
- Dynamic resource allocation based on predefined security postures.
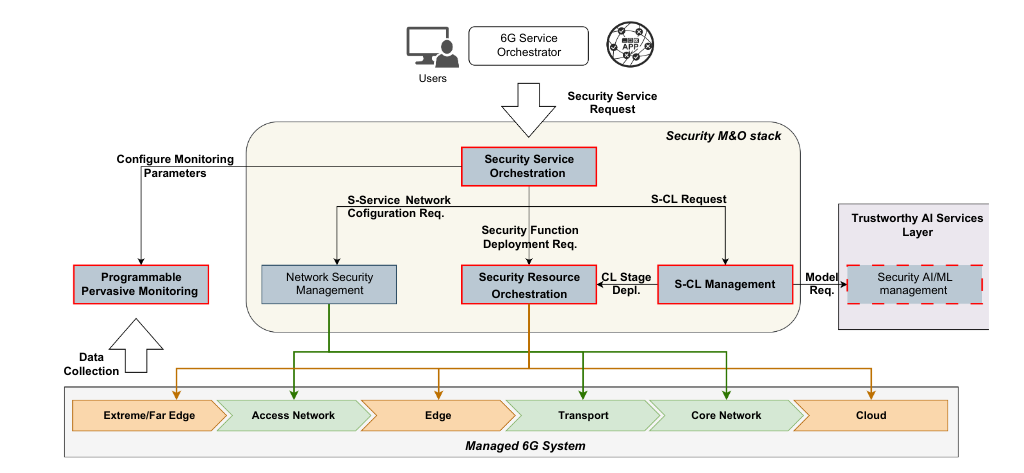
ROBUST-6G Zero-touch security platform functional architecture
2. Programmable Pervasive Monitoring
Monitoring plays a critical role in detecting and predicting security threats. The Programmable Monitoring Platform (PMP) is designed to collect data across multiple layers of the 6G ecosystem, including the cloud, edge, and far-edge environments. This platform’s programmability ensures that monitoring configurations can be tailored to the unique needs of stakeholders.
The PMP could be designed to support extensibility and programmability, potentially allowing new monitoring tools or components to be added without altering its core architecture. Also, it can focus on efficiently aggregating and pre-processing data to optimise resource use and minimise redundancy. Another important characteristic to be contemplated in a PMP solution is related to communication security, which may include the data transmission between the internal components and the external parts of the closed-loop to avoid information exposure. Additionally, the system may dynamically adjust the configuration of its components to meet changing needs or conditions. These objectives will provide competencies to design a PMP to manage future challenges in distributed networks over the Cloud Continuum.
The PMP supports:
- Real-time data exposure for threat detection.
- Historical data storage for AI/ML model training.
- Integration with other modules for a holistic security approach.
The PMP’s ability to configure and adapt its monitoring parameters makes it an essential tool for pre-emptive threat management.
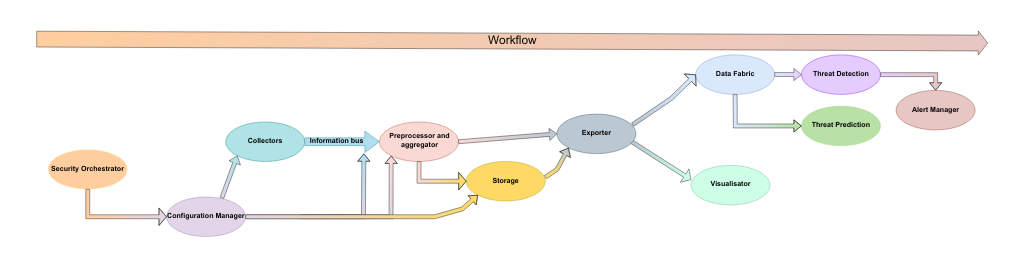 Workflow of the Programmable Monitoring Platform
Workflow of the Programmable Monitoring Platform
3. Threat and Anomaly Detection and Prediction
The use of advanced AI/ML models enables the Zero-Touch Security Platform to predict potential threats before they materialize. This predictive capability is vital for maintaining the integrity of the network and minimizing disruptions.
Features of this pillar include:
- AI/ML-driven anomaly detection using historical and real-time data.
- Proactive measures to address identified vulnerabilities.
- Continuous refinement of detection models based on new data.
Predictive security ensures that the platform remains ahead of emerging threats, providing a robust defence against sophisticated cyberattacks.
4. Closed-Loop-Based Security Automation
At the heart of the Zero-Touch Security Platform is the concept of security closed loops. Based on the ETSI Zero-Touch Service Management (ZSM) framework, these closed loops automate security processes through four key stages:
- Monitoring: Collecting and analysing data from managed entities.
- Analysis: Identifying anomalies and determining potential responses.
- Decision: Selecting and prioritising actions based on analysis.
- Execution: Implementing corrective actions to maintain security levels.
These loops can function autonomously or with human oversight (human-in-the-loop) when necessary, ensuring both efficiency and accountability. The flexibility of this approach allows it to adapt to the varying needs of 6G stakeholders.
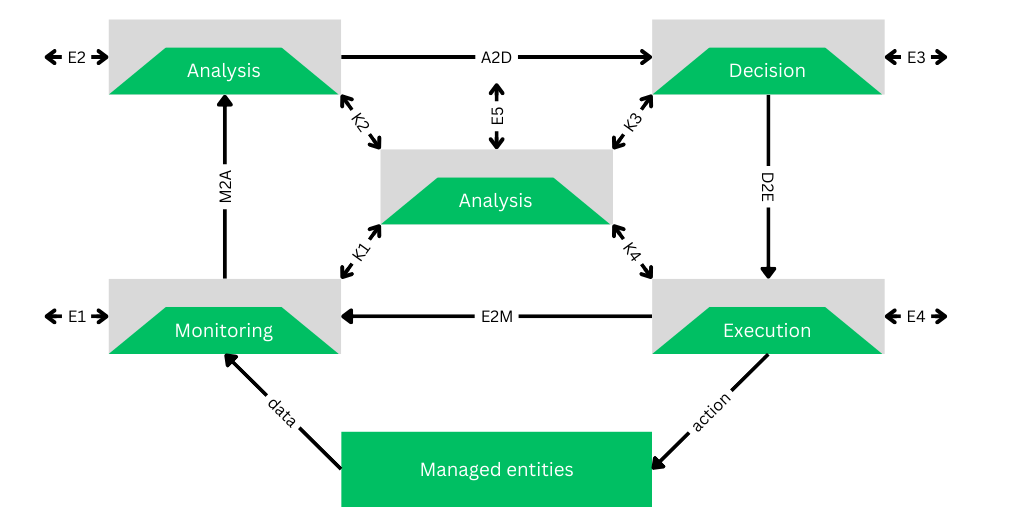 Functional view of a Closed-Loop and its stages within the ZSM framework [ZSM009-1-2023]
Functional view of a Closed-Loop and its stages within the ZSM framework [ZSM009-1-2023]
Architectural Insights: From Concepts to Implementation
Deliverable 4.1 also introduces the functional architecture of the Zero-Touch Security Platform. The architecture integrates modules such as the Security Orchestrator, Security Resource Orchestrator, and Closed-Loop Management to create a cohesive system capable of handling the complexity of 6G networks. One notable feature is the adoption of an ontology-driven approach within the Security Orchestrator. By leveraging ontologies, the orchestrator can reason over available security resources, enabling optimal decision-making.
The architecture also highlights:
- Collaboration with a Data Management Layer for seamless data exposure.
- Integration with AI/ML Service Layer for enhanced transparency and reliability.
- Modular design to support scalability and flexibility across use cases.
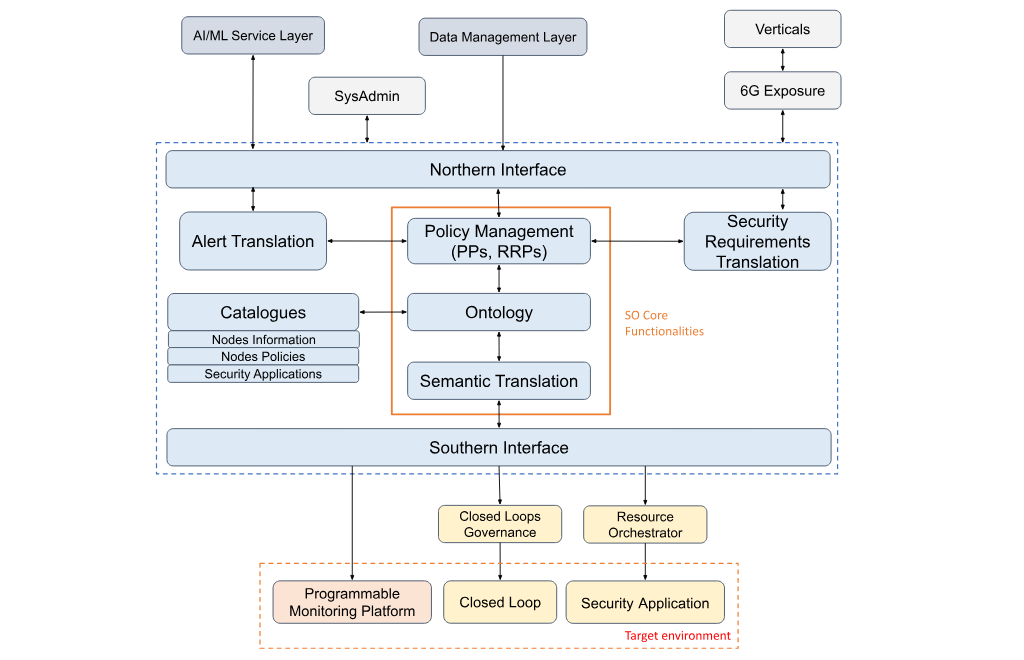 Zero-touch Security Orchestrator Functional Architecture
Zero-touch Security Orchestrator Functional Architecture
Practical Applications and Future Directions
The vision outlined in Deliverable 4.1 is not limited to theoretical constructs; it is firmly rooted in the practical applicability of the proposed solutions. The initial prototypes of the platform’s components are expected to be deployed in the second year of the project.
Additionally, the deliverable outlines plans for continuous refinement through feedback loops, ensuring that the platform evolves alongside emerging 6G technologies and threats.
Conclusion: Pioneering Secure 6G Ecosystems
ROBUST-6G Deliverable 4.1 marks a significant step forward in redefining security for next-generation networks. By leveraging automation, predictive analytics, and closed-loop mechanisms, the Zero-Touch Security Platform addresses the challenges of securing 6G systems in multi-domain, multi-stakeholder environments.
As the project progresses, subsequent deliverables will provide deeper insights into the platform’s development and implementation and integration with other core elements of the ROBUST-6G architecture. With its innovative approach, ROBUST-6G is paving the way for a future where 6G networks are not only faster and more efficient but also inherently secure and resilient.
Stay tuned for further updates as the project continues to revolutionize 6G security!
For more details, visit ROBUST-6G-Deliverables.