As the world transitions towards the sixth generation (6G) of wireless networks, ensuring robust security and trustworthiness solutions becomes a critical necessity. In this vein, the ROBUST-6G project aims to address key challenges related to security and trustworthiness through a comprehensive research and innovative solutions. Concretely, Deliverable 2.2, a cornerstone of this initiative, focuses on defining cutting-edge use cases (UCs), an initial architecture, the dataspace framework for managing 6G heterogeneous data sources, and system requirements.
1. Use Cases for 6G Security
Three primary use cases illustrate the project’s strategic focus, targeting distinct areas to improve the security landscape of 6G networks:
Use Case 1: AI model trustworthiness evaluation for 6G distributed scenarios
The first use case focuses on the critical need for secure and trustworthy AI systems within 6G networks. The explosion of data-driven applications and services in 6G scenarios demands AI/ML models that are robust, explainable, and fair. So as to investigate the previous pillars, this use case is going to explore crucial fields such as:
- Decentralized Federated Learning (DFL): Traditional centralized AI training methods often require data to be collected and processed in a central location, raising significant privacy concerns and a central bottleneck when solutions expand drastically. In contrast, DFL removes the need for a central server, allowing direct peer-to-peer collaboration between participants, ensuring that sensitive information never leaves its origin. Instead, model updates are shared and aggregated, preserving privacy while enabling collaborative AI model training.
- Explainability and Fairness: A major concern in AI systems is their “black-box” nature, which makes them difficult to interpret. This use case emphasizes explainable AI (XAI) techniques that provide transparent insights into how decisions are made. Fairness mechanisms are integrated into AI systems to identify and mitigate biases that may arise during model training or deployment. These mechanisms ensure that AI systems operate in a non-discriminatory manner.
- Sustainability: Sustainability in AI involves optimizing computational resources to reduce energy consumption and environmental impact. The proposed approach incorporates energy-efficient algorithms and processing techniques to align with the green goals of 6G.
- Physical Layer Security: Ensuring AI models’ security extends beyond software-based measures to include robust protection at the physical and sensing layers. In this UC, trustworthiness measures from the infrastructure layer are integrated, leveraging AI models for authentication, secret key agreement, and threat detection. The approach includes analyzing RF signatures, engineered RF fingerprints, and agent positions to enhance security mechanisms. Additionally, techniques such as secure modulation and encryption at the physical communication layer contribute to mitigating potential attacks.
By implementing these elements, this use case aims to provide a robust framework for training and deploying AI models that are both secure and socially responsible.
Use Case 1 consists of two scenarios:
Decentralized Federated Learning for Joint Privacy-Preserving AI/ML Model Training
This scenario focuses on developing a fully decentralized federated learning (DFL) framework for training AI/ML models in a privacy-preserving manner across distributed 6G networks. Instead of relying on centralized servers, participating network nodes (cloud, edge, and extreme edge) collaboratively train and refine AI models while maintaining data privacy. The trustworthiness of models is assessed based on key aspects such as robustness, explainability, fairness, and accountability. A reputation-based trust mechanism is introduced to weigh or filter model updates from different entities based on past behavior. The goal is to improve AI/ML model accuracy and robustness while ensuring data security and fairness, ultimately achieving trust scores above 80% and robustness scores above 85% against adversarial attacks.
Physical and Sensing Layer Trustworthiness and Resilience
This scenario extends AI trustworthiness to the physical and sensing layers of 6G networks, integrating security mechanisms such as authentication, secret key agreements, and threat detection using AI-driven probabilistic models. Data is collected from sensors, RF signatures, and distributed MIMO systems to improve authentication accuracy, enhance secure communication, and prevent adversarial attacks. AI models are used to determine message authenticity and generate encryption keys based on physical channel randomness. The approach aims for over 90% authentication accuracy, a key agreement rate above 99%, and an 80% accuracy in detecting threats using RF fingerprinting, ensuring enhanced security and resilience in 6G networks.
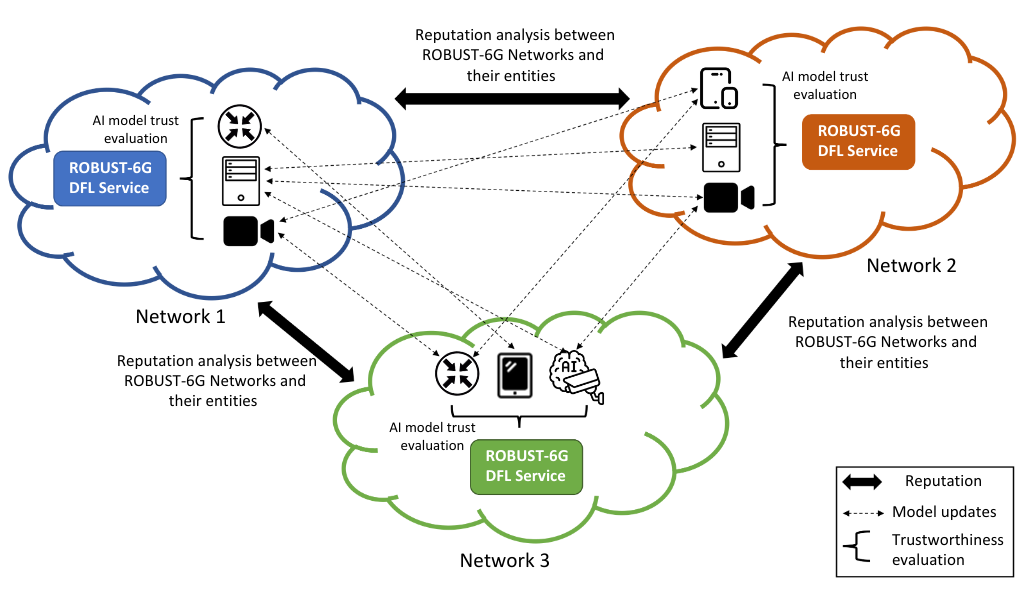 AI model trustworthiness evaluation diagram for 6G distributed scenarios
AI model trustworthiness evaluation diagram for 6G distributed scenarios
Use Case 2: Automatic threat detection and mitigation in 6G-enabled IoT environments
The second use case addresses the increasing security challenges posed by the proliferation of IoT devices in 6G networks. With billions of devices interconnected, ensuring seamless and secure operations is critical. This use case introduces:
- AI-driven Closed-loop Threat Management: Advanced AI algorithms are employed to continuously predict and detect suspicious IoT network activity. The closed-loop approach ensures that threats are not just detected but are also addressed in real time without manual intervention. This capability is particularly vital for mitigating fast-evolving cyberattacks.
- Diverse Threat Scenarios: The use case outlines multiple IoT-specific threat scenarios, including:
- Economic harm caused by malicious actors manipulating IoT systems.
- Fraudulent usage of IoT services leading to unauthorized financial gains.
- Cyber-physical threats where IoT devices are exploited to compromise physical infrastructure.
- Proactive Defense Mechanisms: Rather than relying solely on reactive strategies, this use case integrates proactive mechanisms to anticipate and mitigate potential threats. For instance, anomaly detection models can identify unusual patterns in network traffic that may signal an impending attack.
The integration of AI into IoT security management aims to create resilient IoT environments capable of self-healing and adapting to new threats.
Use Case 2 consists of three scenarios:
Device Violation to Cause Economic Harm (Office Environment):
In this scenario, an attacker gains unauthorized access to an IoT management platform in a small to medium-sized office and issues seemingly benign commands, such as turning on the heating system during non-working hours. This results in energy waste, potential equipment damage, and even cascading supply chain issues. The security system employs a closed-loop approach, continuously monitoring device activity and environmental conditions to detect anomalies, analyze threats, and take countermeasures such as blacklisting the attacker or shutting down compromised systems.
Fraudulent Usage of Device Resources (Smart Building):
This scenario explores cryptojacking attacks in a smart building where an attacker hijacks IoT devices to mine cryptocurrency, leading to high CPU consumption and increased network traffic. The attack is difficult to detect as compromised devices appear to function normally. The security system uses two closed loops—one monitoring device behavior and another analyzing network traffic—to identify abnormal resource usage and mitigate the attack by isolating compromised devices, blacklisting the attacker, or resetting the IoT platform.
Device Violation to Cause Economic Harm (Smart Agriculture):
In this scenario, an attacker manipulates sensor readings in a smart farm, causing automated irrigation and heating systems to operate incorrectly. This results in significant agricultural losses and resource waste. Since fields are interconnected, the attack can spread, impacting multiple sites. The ROBUST-6G security solution employs multiple closed loops to cross-check sensor data using external sources like meteorological services and applies countermeasures such as RF fingerprinting, frequency hopping, and beamforming to detect and mitigate both data manipulation and physical-layer attacks.
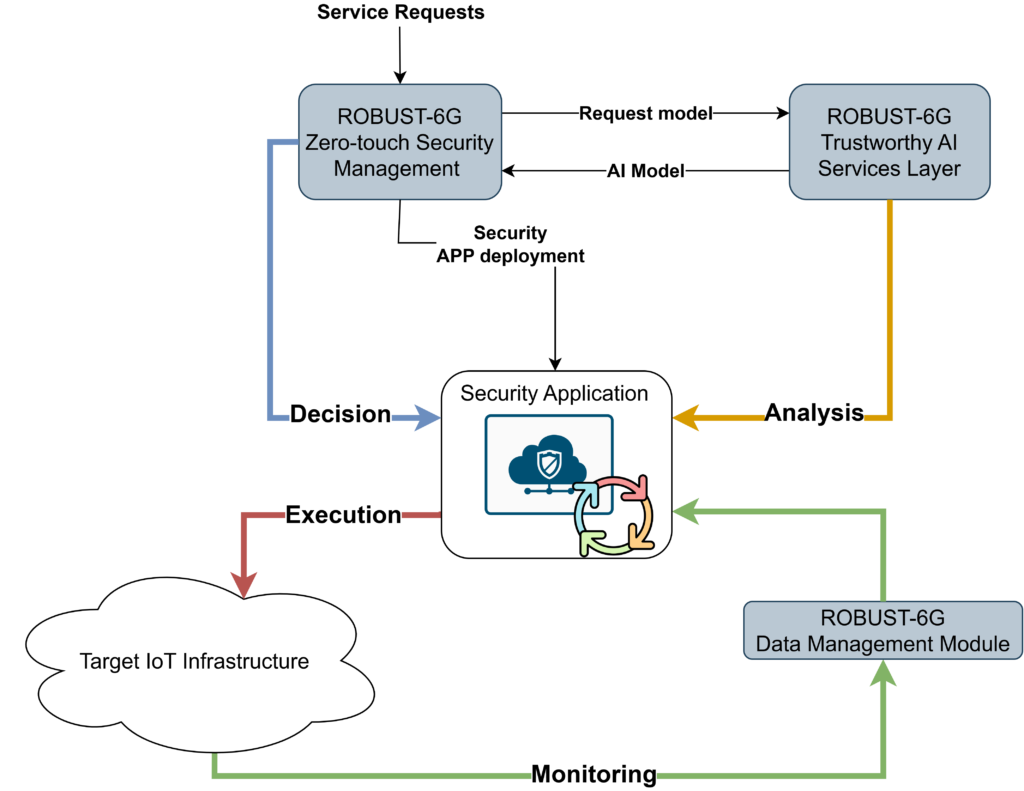 ROBUST-6G components interacting with the external world
ROBUST-6G components interacting with the external world
Use Case 3: Security capabilities exposure with Network-Security-as-a-Service (NetSecaaS)
The third use case introduces the concept of delivering security as a service, leveraging the Open Gateway initiative. This approach democratizes access to advanced security features, making them accessible to a broader range of users and organizations. In this regard, this UCs copes with key components and functionalities like:
- Integration with the Open Gateway Framework: The Open Gateway initiative provides a standardized interface for integrating security services directly into third-party applications. This allows developers to incorporate high-level security features without requiring in-depth security expertise.
- Scalability and Adaptability: The NetSecaaS model is designed to scale with the demands of its users. Whether it’s a small-scale application or a large enterprise network, the service adapts dynamically to provide the required level of security.
- Advanced Security Features: Key offerings under this service include:
- Dynamic threat detection and mitigation tailored to the application’s specific needs.
- Role-based access control (RBAC) to manage permissions and secure sensitive resources.
- End-to-end encryption to ensure data confidentiality during transmission.
- Ease of Use: By abstracting the complexity of security protocols, NetSecaaS empowers organizations to implement advanced security measures without significant upfront investment or technical expertise.
This use case reflects a shift toward security solutions that are not only robust but also user-friendly and cost-effective, enabling widespread adoption across diverse industries.
Use Case 3 consists of one main scenario:
Use Case 3 demonstrates the integration of ROBUST-6G security capabilities into third-party applications using the Open Gateway framework, with a Proof of Concept (PoC) deployed in the 5TONIC lab. The scenario sets specific KPIs for performance evaluation, including an average API call latency of 300ms and a maximum of 1s, API CPU usage below 30%, and at least 50% of ROBUST-6G’s security capabilities exposed through standard CAMARA APIs. To achieve these objectives, the focus will be on optimizing processes and infrastructure to reduce latency and resource consumption while ensuring seamless integration of security capabilities. The scenarios are designed for users with limited network security expertise, such as school network administrators and mobile application developers, demonstrating the practical benefits of Network Security-as-a-Service (NetSecaaS) by addressing their high-level security needs and validating the effectiveness of ROBUST-6G’s advanced security measures.
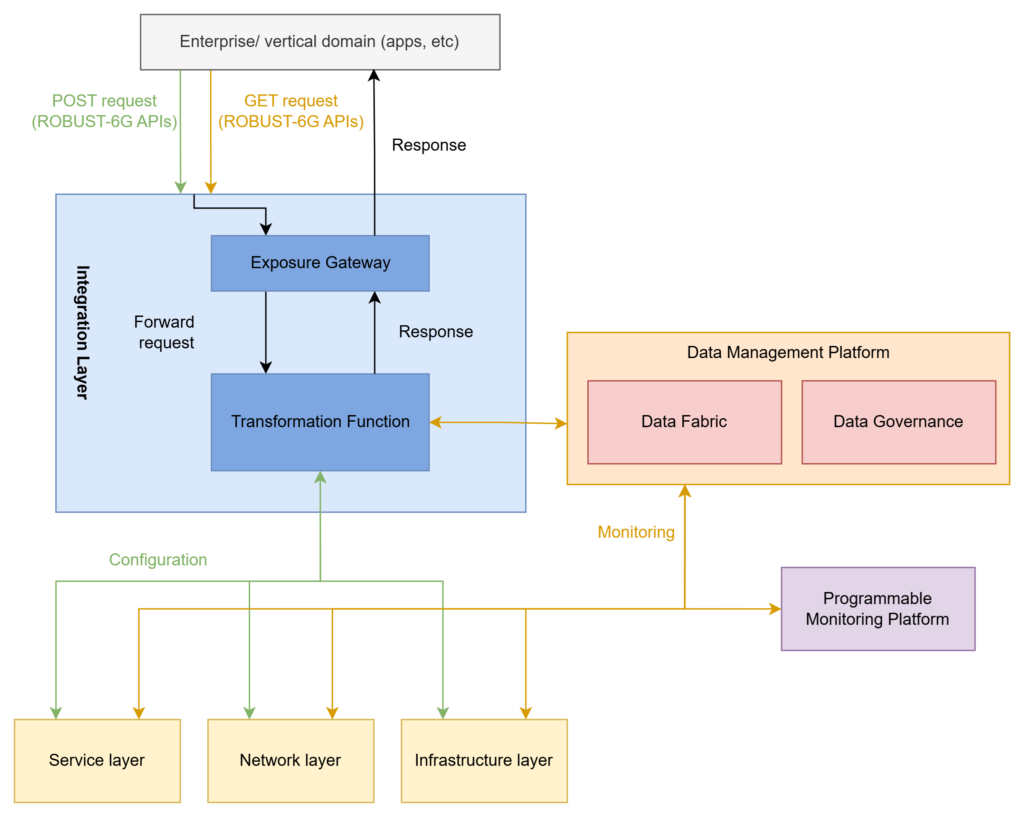 Use Case 3 system architecture
Use Case 3 system architecture
2. ROBUST-6G System Architecture
The system architecture outlined in Deliverable 2.2 is designed to support the complex demands of secure 6G networks. The most relevant architectural components include in the ROBUST-6G system architecture are:
- Programmable Monitoring Platform (PMP): Acting as the eyes and ears of the network, the PMP collects and analyzes data across physical, virtual, and application layers. This platform is vital for feeding real-time threat detection and response algorithms.
- Data Management Platform: Responsible for handling secure data flow between data sources and authorized consumers.
- Zero-Touch Security Management Layer: The automation of security operations through AI and machine learning reduces human intervention, streamlining threat detection and prediction, resource orchestration, and resource optimization.
- Trustworthy and Sustainable AI Services Layer: By embedding trustworthiness into AI workflows, the architecture addresses concerns of reliability, explainability, and robustness. Techniques like federated learning ensure privacy-preserving collaboration across distributed networks.
- Network Layer: A strong emphasis is placed on securing the foundational communication layers. Methods such as advanced encryption and interference mitigation play crucial roles in protecting data integrity and confidentiality.
3. Establishing the ROBUST-6G Dataspace
To address the exponential growth of data in 6G networks, ROBUST-6G introduces a dataspace framework. This framework comprises:
- Data Fabric: Responsible for gathering, processing, and storing security-related data, the Data Fabric ensures that all monitored data is available to consumers via a unified, secure interface. It facilitates seamless data integration across diverse and heterogeneous sources such as relational databases, data streams, and APIs.
- Data Governance: This building block is composed of the following components:
- Data Catalog: Provides a registry of the data products available within the data space, allowing users to find and access data according to predefined policies. The Data Catalog promotes data democratization by providing mechanisms for users to discover available data, while improving the quality, privacy, and trustworthiness of the catalogued data.
- Data Security: Enforces robust access control policies that align with the security requirements specified by data product owners, determining precisely who can access specific types of data and under what conditions. By implementing stringent security protocols, it ensures full compliance with privacy, security, and regulatory standards.
Together, these components align with FAIR principles (Findable, Accessible, Interoperable, and Reusable), promoting transparency, scalability, and collaboration across stakeholders in 6G ecosystems.
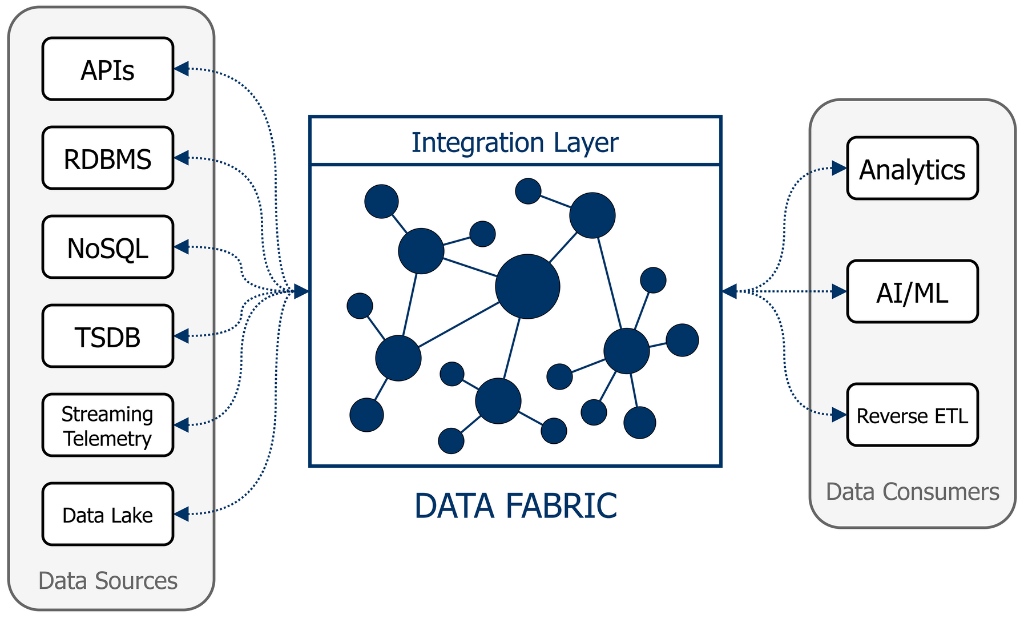 Data Fabric architecture
Data Fabric architecture
4. Comprehensive Requirements Analysis
Deliverable 2.2 accurately defines a set of functional and non-functional requirements to guide the project’s technological and architectural development during the design, development, and validation phases. These requirements span four critical domains:
- Data Management and Governance: Emphasizing secure, compliant, and efficient data handling across distributed networks.
- Distributed AI-driven Security: Leveraging advanced AI techniques to enhance network security capabilities.
- Zero-Touch Security Management: Automating security operations for increased efficiency and reduced human intervention.
- Physical Layer Security: Establishing robust security measures to protect the foundational layers of communication.
By addressing these domains, the project lays the groundwork for a secure and trustworthy 6G ecosystem, ready to meet the challenges of tomorrow.
Conclusion: A Path Towards Secure 6G Networks
Deliverable 2.2 sets a robust foundation for achieving the ROBUST-6G project’s vision. By addressing the complexities of 6G through use case-driven research, modular architecture, and advanced data management strategies, the project takes a significant step toward realizing secure and trustworthy next-generation networks.
Stay tuned as the ROBUST-6G consortium continues to deliver groundbreaking solutions, shaping the future of 6G security and trust.
For more details, visit ROBUST-6G-Deliverables.